Brox: A Framework for Security and Privacy Detection
Introduction
Security and privacy problems have been receiving an increasing attention recently due to the popularity of smartphones. There are many malicious behaviors in applications, especially in Android platform which has many third-party apps. To address the privacy leakage problem in Android platform, we proposed a privacy and security detection tool named Brox.
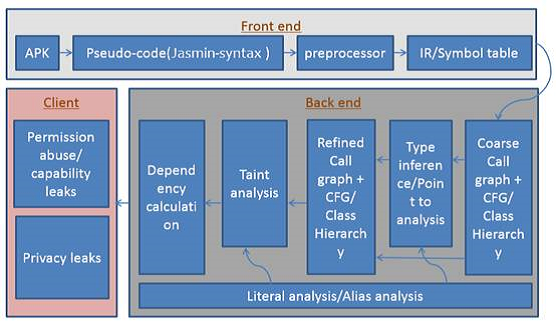
Brox is based on dalvik-opcode specification, which uses data flow analysis framework equipped with flowsensitive, context-sensitive, and inter-procedure techniques to detect potential information leakage path in Android malicious applications. Specifically, Brox uses inter-procedure analysis and dependency calculation to understand the intention for each sensitive operation. By using reachable analysis, Connection between privacy access operation and leakage operation can be established.
System Design
Privacy Attack Model
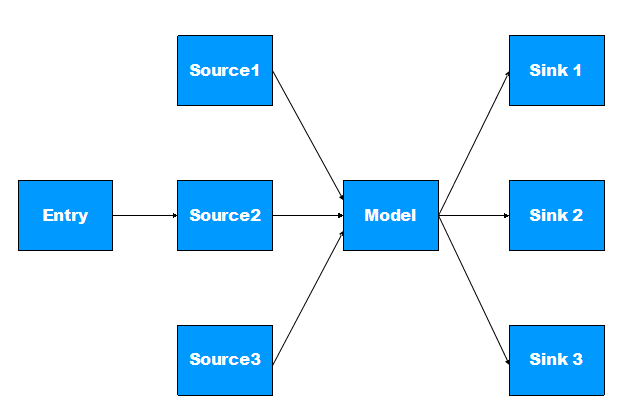
We have manually analyzed android malicious applications and noticed that most malicious applications’ risky behaviour focus on collecting and sending the users’ private information.
Like figure 1, we define the following specific behaviours as the potential privacy leaks of Android application.
- Collect user’s private information using android framework API.
- Transform private information into another form.
- Send the transformed information to remote phone or remote server.
In the attack model, we define Entry as the triggering action which leads to privacy leak, Sources as the action which collects sensitive information, Sinks as Privacy sending action. A path connecting a source and a sink is regarded as a Confirmed path.
Working Mechanism
Brox first extracts Android applications into pseudo-code by using Dedexer and then perform analysis on the pseudo-code. There are several steps of the whole process.
- Build the call graph and acquire the parameter.
- Identify the triggered events to find the Sink action.
- Proceed backward slicing to find the Source information and
confirm the privacy leakage path.
Demo
Brox can detect most of malicious actions of Android applications, and is able to generate an elaborate report of privacy leaks in Android applications.
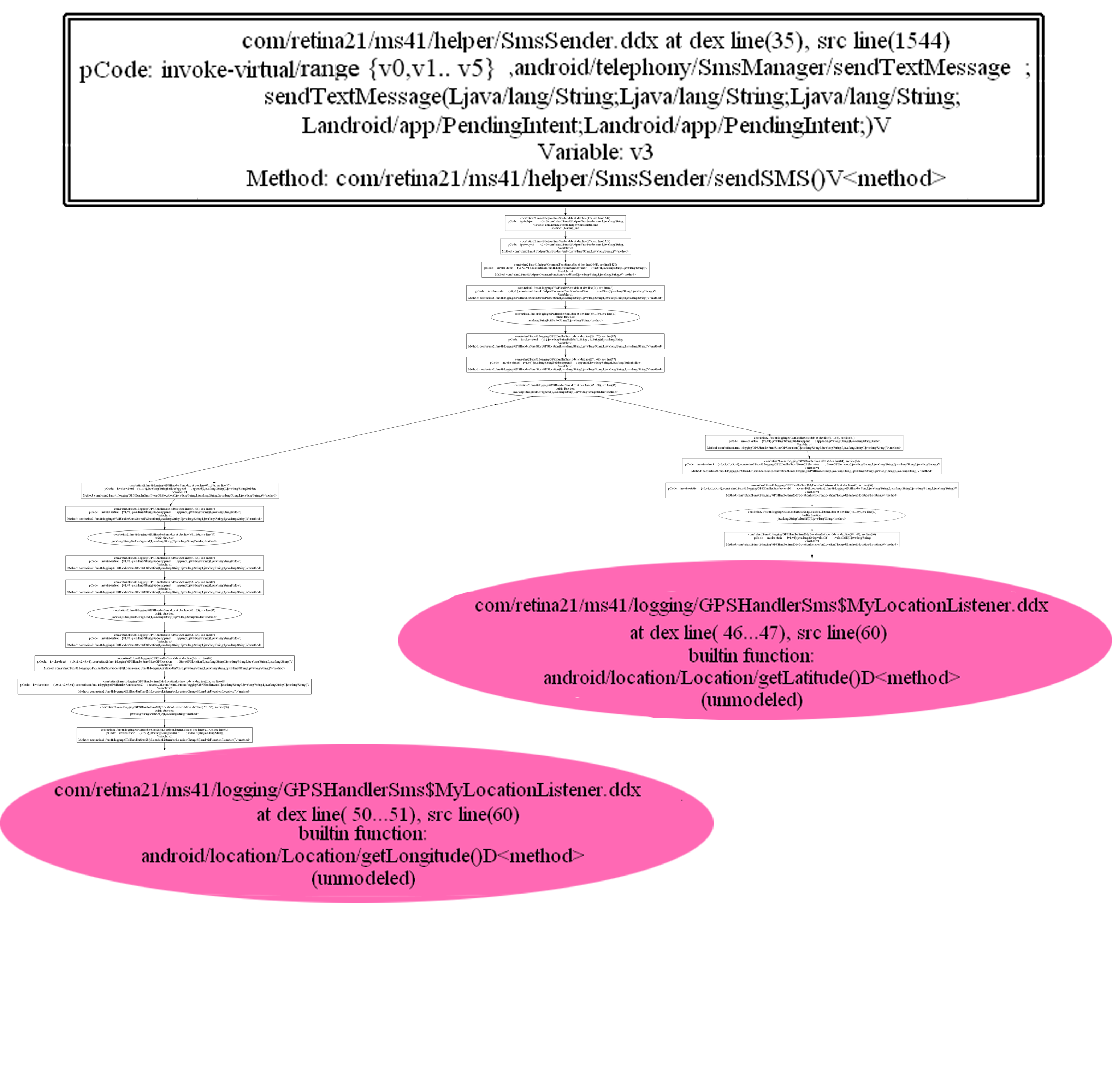
Fig. 3 is the analysis results automatically generated by Brox for Mobile Spy. The node surrounded by two lines stands for the sending action. The picture shows that the application sends the privacy information via sendTextMessage API. The variable label represents data dependency.
The first node with label "v1" indicates that the sending information is stored in the "v1" register, and the edge linked to "v1" stands for that the "v1" register depends on the parameter of "sendSMS". Thus, we can determine that "sendSMS" is the Sink action. The malware acquires the user’s location information by using getLatitude and getLongitude API, which is the source of privacy leak and colored with pink. Obviously, a confirmed path exits in Fig. 3. The result shows that this malware sends user’s location information through SMS without the permission of users.
Publication
Our paper Detecting GPS Information Leakage in Android Applications was accepted by GLOBECOM 2013.